About meAbout
I graduated from the University of South Carolina in 2020 (Go Gamecocks!). Over the past 5+ years, I have gained experience in the various sides of the insurance industry. Beginning as an account manager, being promoted to a retail agent, advancing to a broker, and currently serving in a leadership position on a high-performing underwriting team.
I bring a strong foundation in project management, team leadership, and client consultation to your team. My career has been built on cultivating high-value relationships, driving collaborative growth strategies, and aligning cross-functional teams to deliver measurable outcomes.
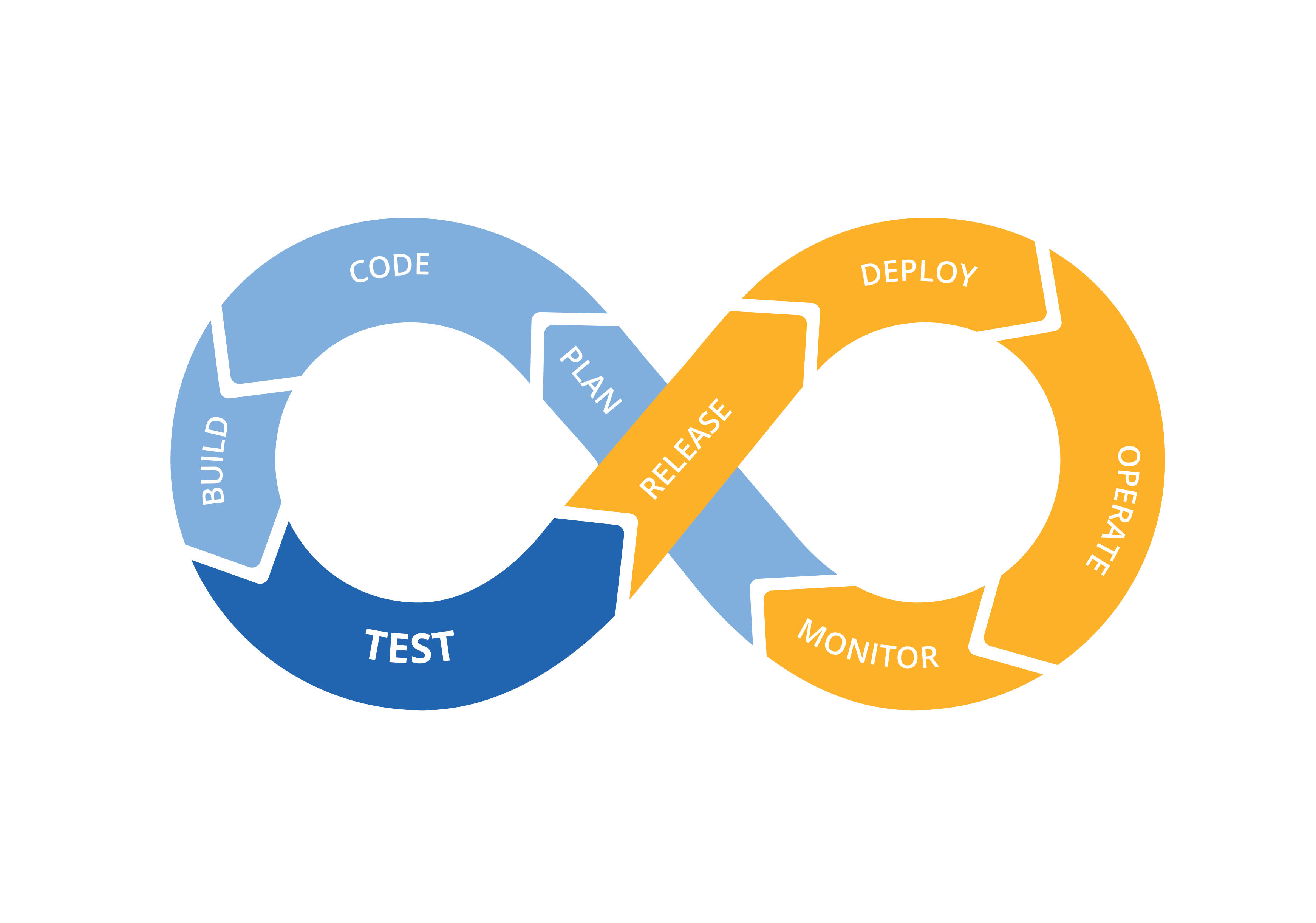
A self-starter who is always looking toward the future, I have hands-on experience with the today's most popular security tools such as Splunk, Wireshark, nmap, tcpdump, and Metasploit. The CompTIA Security+ and Google Cybersecurity Professional Certificates prove my understanding of IT security. In addition, I am actively pursuing the AWS Certified Solutions Architect Associate. I have built many projects in the cloud and am familiar with optimizing cloud-based architecture through projects such as the AWS Cloud Resume Challenge.
Check some of them out while you are here by navigating to "projects" or "blogs" section!
BY THE NUMBERS
5+
Years of
Experience
$1M+
New Business
Premium
4
Professional
Certifications
10%
Sales
Growth
300+
Happy
Clients
5 Star
Customer
Reviews
MY TIMELINE
March 2025 - Current
Associate Team Leader - CRC Group
In my current role as an Associate Team Leader at CRC Group, I support a high-performing underwriting team and serve as a key liaison between leadership, internal stakeholders, and strategic partners. I frequently advise agents, lead escalations, and ensure timely, accurate delivery of complex solutions. I have brokered submissions through the full sales cycle, closing over $250K+ in new business premium in 6 months.
August 2022 - October 2024
Account Executive - Stacks Brokerage Corp
As the 1st employee hired outside the state of Florida, I successfully established a strong presence in my region. Sold over $850K in new business premium, acheiving 10% sales growth YoY. Built and managed a book of business with over 50+ clients. Collaborated with Partner of the Brokerage to quote, negotiate, and close a $1.1M account.
January 2022 - July 2022
Account Executive - Taylor Agency
Spearheaded lead generation efforts, building a network of prospects through conducting 20+ cold calls daily, utilizing social media, and CRM optimization. Worked closely with sales leadership to develop strategic sales plan that resulted in accomplishing a portfolio of $150K+ in new business premium.
July 2020 - December 2021
Account Manager - Taylor Agency
Collaborated with internal team to manage and grow a book of business with 300+ clients. Provided customer support, executed policy changes, facilitated claims, closed cross selling opportunities, and managed renewals. Accomplished a 90% retention rate, 5% above industry average.
January 2020 - May 2020
Intern - University of South Carolina Football
Assisted the Director of Player Personnel with recruiting efforts, including managing the recruiting database, creating recruiting materials, and organizing recruiting events. Assisted coaching staff with coordinating practice schedule. Delivered correspondence to staff members.
August 2016 - May 2020
B.S. - University of South Carolina
Graduated with a 3.4 GPA, majoring in Sports, Entertainment, and Event Management.
My Certificates & SkillsCertificatesSkills
Technical Skills
Transferable Skills
My PortfolioPortfolio
Check out some of my Projects!
My BlogsBlogs

Creating an End-to-End AWS Web Application Calculator
Follow along this tutorial to create a simple calculator using an HTML text editor, AWS Amplify, Lambda, DynamoDB, API-Gateway, and IAM.

Python Allow List Algorithm
For this project, I am a security analyst for a health care company. As part of my job, I am required to regularly update a file that identifies the employees that are allowed to access restricted content. The contents of the file are based on who is working with personal patient records. Employees are restricted access based on their IP address. I am tasked to create an algorithm that uses code to check whether the allow list contains any of the addresses from the remove list.

Investigating security incidents with Splunk, Suricata, and Chronicle
In this scenario, I am a security analyst who muct monitor traffic on my employer's network and investigate incidents. I was provided tutorial data which resides in the tutorialdata.zip folder in the project files. First, I monitored the network traffic using Suricata and configured a custom rule to trigger alerts. Next, I analyzed the traffic using Splunk's SPL querying language and isolated failed SSH login attempts for the root account. Lastly, I used Chronicle to investigate an alert for a phishing incident and determined whether any other employees have visited the compromised domain.
.png)
Capturing and analyzing network traffic with Wireshark and Tcpdump
In this scenario, I am a security analyst who must capture and analyze live network traffic from a Linux virtual machine using tcpdump. I will then use Wireshark to filter the captured traffic and answer questions about the data.

Botium Toys Security Audit
This project is based on the fictional company "Botium Toys". The manager of the IT department has determined that an internal audit needs to be conducted. The manager implements the NIST CSF to establish the audits scope and goals. My task is to review the IT manager's scope, goals, and risk assessment report then, perform an internal audit by completing a controls assessment checklist. I will then check to see if Botium Toys is adhering to PCI DSS, GDPR, and Organizational compliance best practices.
Contact MeContact
Contact me here!
Think I will be a great fit for your team? Reach out to me here!
: Charleston, South Carolina
: ejh2@proton.me
: University of South Carolina
: (678) 899-3119





.png)
.png)